Artificial Intelligence
Take Full Control of Your Digital Access with Our Identity and Access Management (IAM) Service
Are You in Control of Your Digital Doors or Are They Wide Open?
Table of Contents
- 1 Are You in Control of Your Digital Doors or Are They Wide Open?
- 2 What Is Identity and Access Management (IAM)?
- 3 What Makes Our IAM Service Different?
- 4 Here’s What You’ll Gain with Our IAM Service
- 5 Is This IAM Solution Right for You?
- 6 Here’s How Our IAM Implementation Works
- 7 Results That Speak for Themselves
- 8 Trusted by the Best in Tech
- 9 Your Next Step Starts Here
- 10 Ready to Secure Your Digital Future?
In today’s hyper-connected world, unauthorized access, password fatigue, audit failures, and insider threats are more than just IT issues they’re existential threats to your business.
Manual user provisioning, legacy systems, and inconsistent access policies expose your organization to costly data breaches, regulatory violations, and operational chaos.
We get it you need to secure your systems without slowing down your team. That’s where our Identity and Access Management (IAM) Service steps in: giving you total visibility, control, and confidence over who accesses what, when, and how.
 What Is Identity and Access Management (IAM)?
What Is Identity and Access Management (IAM)?
IAM is more than just logging in it’s the backbone of secure digital operations. It ensures that only the right people access the right resources at the right time, for the right reasons.
From onboarding new employees to removing access when roles change or users leave, IAM keeps everything clean, controlled, and compliant.
But not all IAM services are created equal.
Ours is built with your business in mind.
What Makes Our IAM Service Different?
We combine industry-leading security frameworks with real-world business insights to deliver a solution that works for your unique environment.
✅ Zero Trust Architecture
We enforce least-privilege access across every layer of your environment. No assumptions. No backdoors. Just clean, segmented, verifiable control.
✅ Seamless Integration
Whether you use cloud platforms like Microsoft Azure, AWS, or maintain a hybrid environment, we plug right into your tech stack without disruption.
✅ End-to-End Identity Lifecycle Automation
From onboarding to offboarding, we automate every stage of the user journey reducing errors, saving time, and eliminating access creep.
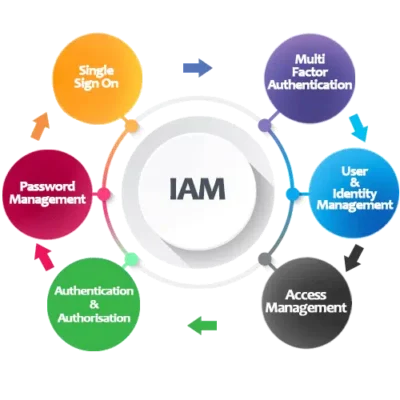
 Here’s What You’ll Gain with Our IAM Service
Here’s What You’ll Gain with Our IAM Service
Stronger Security, Fewer Breaches
Enforce centralized policies, detect anomalies, and eliminate unauthorized access with real-time monitoring.
⚙️ Smarter User Management
Auto-provision users across systems and revoke access instantly when needed no more manual bottlenecks or forgotten accounts.
Stress-Free Compliance
Generate detailed audit logs and reports to meet GDPR, HIPAA, ISO 27001, and other regulatory requirements with ease.
Reduced IT Workload
Lower your IT overhead by enabling self-service password resets, access requests, and smart role-based policies.
Remote-Work Ready
Empower your distributed workforce with secure single sign-on (SSO), identity federation, and adaptive authentication.
Scalability for Tomorrow
Whether you’re onboarding 10 users or 10,000, our IAM grows with you across new apps, devices, and geographies.
Is This IAM Solution Right for You?
This service is a perfect fit if you are:
A mid-to-large enterprise managing a growing workforce and complex system access
In a regulated industry such as healthcare, finance, education, or government
A CIO, CISO, or IT Manager responsible for audit readiness and cybersecurity
Migrating to or managing a hybrid/multi-cloud infrastructure
Tired of manual access control chaos and want automation + clarity
Here’s How Our IAM Implementation Works
Our structured, streamlined process ensures minimal disruption and maximum value:
Assessment & Discovery
We audit your current access environment and identify security gaps.Custom Strategy & Design
We create a scalable, secure IAM framework tailored to your business needs and regulatory requirements.Integration & Deployment
We connect your systems, apps, and user directories to enable unified access control fast and reliably.Training & Enablement
We train your teams and IT staff, so they feel confident managing the system.Ongoing Optimization
As your business evolves, so does your IAM. We continuously support, monitor, and improve your environment.
Bonus: You’ll receive a quarterly IAM health report to track improvements, risks, and opportunities.
Results That Speak for Themselves
✅ 3x faster onboarding across departments
✅ 70% fewer IT support tickets related to access issues
✅ 100% audit pass rate in the last four quarters
✅ Significant cost savings through automation and reduced human error
Trusted by the Best in Tech
We bring the credentials and partnerships that matter:
✔ Microsoft Identity & Access Partner
✔ AWS Security Competency
✔ ISO 27001 Certified Implementation Team
✔ Proven track record across finance, healthcare, logistics, and enterprise SaaS
“They transformed our user access environment in weeks not months. IAM used to be a headache. Now it’s a strategic asset.”
— James L., Director of IT, Global Logistics Firm
Your Next Step Starts Here
Don’t wait until the next audit failure or security incident to act. Take the first step toward a secure, compliant, and future-ready digital identity framework.
Schedule a Free IAM Consultation Today
Download Our IAM Capabilities Brochure
Request a Live Demo of Our IAM Solution
See Transparent IAM Pricing Options
Ready to Secure Your Digital Future?
Our IAM service isn’t just a tool it’s your strategic defense against the threats of tomorrow. Let’s build your identity framework the right way, right now.
#IAM #CyberSecurity #AccessManagement #DigitalSecurity #ZeroTrust #CloudSecurity #ComplianceReady #ITSolutions #IdentityGovernance #IAMSolutions #EnterpriseSecurity















































































 Here’s What You’ll Gain with Our IAM Service
Here’s What You’ll Gain with Our IAM Service
Thanks for reading! Stay curious, keep exploring.