ABOUT THE COMPANY


Protect sensitive data, streamline user access, and reduce security risks with our expert IAM solutions.
Is your organization struggling with unauthorized access, inefficient user permissions, or security breaches? Weak identity management exposes businesses to cyber threats, compliance risks, and operational inefficiencies.
Frustration: Employees juggle multiple passwords, slowing productivity.
Risk: Unauthorized access leads to data leaks and compliance violations.
Cost: Manual user provisioning and deprovisioning waste IT resources.
Our Identity and Access Management (IAM) solutions eliminate these challenges by automating security while ensuring seamless access for authorized users.


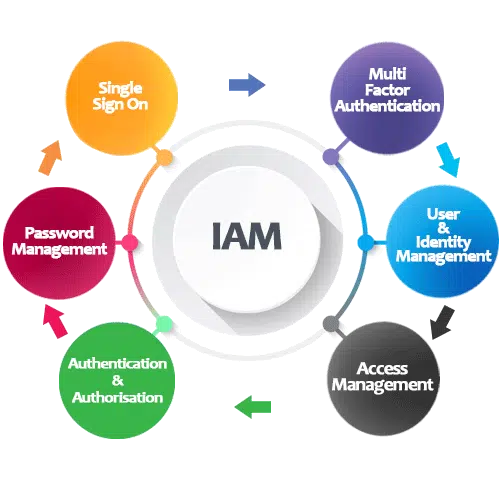
Identity and Access Management (IAM) ensures the right people have the right access to the right resources securely and efficiently.
✅ Enterprise-Grade Security – Protect against breaches with multi-factor authentication (MFA) and role-based access control (RBAC).
✅ Seamless User Experience – Simplify logins with Single Sign-On (SSO) and reduce password fatigue.
✅ Compliance Made Easy – Meet GDPR, HIPAA, SOC 2, and other regulatory requirements effortlessly.
✅ Enhanced Security – Prevent unauthorized access with adaptive authentication.
✅ Increased Productivity – Reduce login friction with SSO and automated workflows.
✅ Cost Savings – Cut IT helpdesk costs by up to 50% with self-service password resets.
✅ Scalability – Grow confidently with cloud-based IAM that adapts to your business needs.
✅ Audit & Compliance – Generate instant access reports for compliance audits.
✅ Mid-to-Large Enterprises needing scalable security.
✅ Healthcare & Financial Services requiring strict compliance.
✅ Remote & Hybrid Workforces needing secure, flexible access.
✅ IT & Security Teams tired of manual user management.
Step 1: Assessment – We analyze your current access controls and security gaps.
Step 2: Custom Solution – Tailor an IAM strategy with SSO, MFA, or Privileged Access Management (PAM).
Step 3: Seamless Deployment – Integrate with your existing systems (Azure AD, Okta, AWS, etc.).
Step 4: Ongoing Support – Monitor, update, and optimize your IAM framework.
✔ Case Study: “Global Bank Reduces Security Incidents by 70% with Our IAM Solution”
✔ Testimonial: “Switching to their IAM system saved us hours in IT overhead while improving security.” – CTO, TechCorp
✔ Certifications: SOC 2, ISO 27001, Microsoft Gold Partner
✔ Trusted By: Logos of well-known clients (if applicable)
